Web and mobile application security and protection from cyberattacks often refer to all solutions aimed at ensuring the utmost safety from malicious attacks.
It's not just about defensive actions but also preventive ones, continuous readiness to fend off an attack and counter its damage.
In the most general sense, application security should be associated with regularly examining the structure and how the application works, searching for vulnerabilities, errors, and shortcomings that can increase the risk of an attack and expose the app to unauthorized access to confidential customer and company data.
However, should thinking about cyberattacks, hackers, application security, security vulnerabilities, data security, damage, risks, and consequences be associated only with already operational applications?
Shouldn't thinking about the security of web and mobile applications start at the stage of choosing a technology stack?
Which technologies are vulnerable to cyberattacks, and which are considered relatively safe or just safer than others?
If you're interested in the security of your applications and learning about the top programming languages, then be sure to read the following article, in which we'll discuss the issues of programming language security.
We invite you to read on!
Thinking about mobile application security — safe technology stack
The choice of technology you will use in a given project isn't easy and sometimes requires thinking through the priorities (business and user-centered) and agreeing to difficult compromises.
A specific set of technology, tools, and solutions is always, more or less, conditioned by an array of factors related to the following:
- Adequacy, efficiency, utility, and long-term nature of a given technology
- Objective effectiveness of security measures
- Business profitability of a given technology and its safeguards
- Adjusting the budget to match the technology and project
- A time frame of the project and the time-consuming nature of the technology in question
- Organizational and resource aspects (e.g., availability of specialists working with a given technology)
- Level of expected and ensured application security.
Every project is a choice. Web and mobile application security requires making tough and not-that-obvious choices.
The selection criteria can be divided into purely objective ones (resulting from rational and unbiased premises) and subjective ones (coming from personal preferences, experiences, and competencies of the development team).
The particular technology stack is the result of what you place special emphasis on.
Unfortunately, the security of a web application or any other digital product isn't always considered a key and strategic factor.
Often security is overshadowed by the following:
- Capabilities of the development team creating the application
- Current technology trends (e.g., regarding the increase in popularity or appearance of new technology in which applications are made)
- The ratio of the quality of the code to the cost of producing it
- Availability of specialists in a given market
- Acceptable level of security that is to be achieved in a given project.
The combination of these conditions influences what level of security (both for the owners of the business and application users) will be implemented in a given software.
Application security issues are also pushed back in time as tasks with lower priority and lower business importance. Issues that therefore are doable in the future.
In many cases, the situation in which the application is minimally safe instead of being maximally secure by default is acceptable.
This approach is supported by the belief that most popular programming languages offer similar levels of security and are similarly "reliable and perfect."
The comparison of different languages in terms of their security raises many controversies (regarding criteria and methodology) and many emotions, often resulting from personal experiences and preferences.
Naturally, conclusive settlement of the superiority of some technologies over others should be carried out based on consistent assumptions, clear methodology, and accurate and diverse criteria.
Only then, making such comparisons, evaluations, and creating hierarchies gives a relatively reliable, fair, and authoritative picture.
Descriptive and tangible benefits from comparisons are more or less useful.
Comparisons aren't only about creating hierarchies and determining winners and losers.
An important matter is to indicate the strong and weak features of a given technology, raising awareness of its potential and areas that can be, but of course, don't have to be, a source of problems with security.
Creating comparisons is also about finding solutions relevant to the security issue, which is complex, multidimensional, context-dependent, time-varying, and subject to adopted priorities.
Finally, comparing is about awareness of which elements need to be improved, which ones need special attention, and which require, metaphorically speaking, special care.
Secure mobile applications or how to measure the security of a programming language?
The issue is certainly not obvious, simple, or devoid of controversies.
Nevertheless, from time to time, companies dealing with security undertake this demanding task and try to answer the following questions:
- How much a given language (and thus the application written in it) is vulnerable to attacks?
- What level of security does a given language offer?
- How is a given technology developed in terms of security?
An excellent example of this kind of practice is the WhiteSource Vulnerability Database.
This database collects information about security vulnerabilities in open-source technology.
It includes over 200 programming languages and over three million components.
However, it's worth remembering that trying to discover how given programming languages deal with security, safeguards, and vulnerabilities is actually an attempt to answer the following questions:
- What types of attacks do you have in mind?
- What attack targets do you have in mind?
- How long resistance to attacks do you want?
- How frequent are the attacks?
- What level of security do you want?
- What kind of threat detection do you have in mind?
- What moment in the development of a particular programming language do you have in mind?
In terms of estimating the level of security offered by a given programming language, the time factor seems to be quite significant.
Programming languages — in particular, those shared and developed under open-source licenses — can differ considerably in this regard.
WhiteSource specialists are obviously aware of this.
As Ayala Goldstein writes in the article "Is One Programming Language More Secure Than The Rest?" most popular programming languages (e.g., C, PHP, Java, JavaScript, Python) have experienced ups and downs over the past decade.
According to Goldstein, although the level of security changed, sometimes significantly, there has also been a clear trend of increasing awareness of security vulnerabilities.
Awareness grew as popularity increased, followed by a much greater commitment of resources.
Active community efforts have helped improve languages in terms of security.
A list of common software vulnerabilities (CWE — Common Weakness Enumeration) has also been created as part of efforts to improve, fix, and patch the vulnerabilities of a given technology.
Communities centered around various programming languages have shown great initiative and awareness of growing problems.
They've also shown great determination in countering security issues.
What is Common Weakness Enumeration?
Comparing languages without referring to indicators that would give a base for evaluations doesn't make sense.
CWE is described and defined as an indicator of security tools, a basis for identifying weaknesses, and a collection of recommendations for repairs and prevention activities.
As you can read in the description of CWE List Version 4.6, it is the work of the community aimed at creating specific and concise definitions for every common type of vulnerability.
Common Weakness Enumeration contains flaws and errors — involving hardware or code — which, if not eliminated, can be a cause or means of launching an attack.
Since 2006 CWE has primarily aimed to educate, diagnose and normalize.
Actions undertaken within the CWE initiative are focused on the following:
- Descriptions of errors
- Diagnosis of software and hardware
- Standardization of repair and diagnostic solutions
- Prevention and creation of repair solutions to protect users.
The main advantage of CWE is the systematization of problems, striving for exhaustive and concrete descriptions of them, and standardization of diagnostic and comparative tools that determine quality.
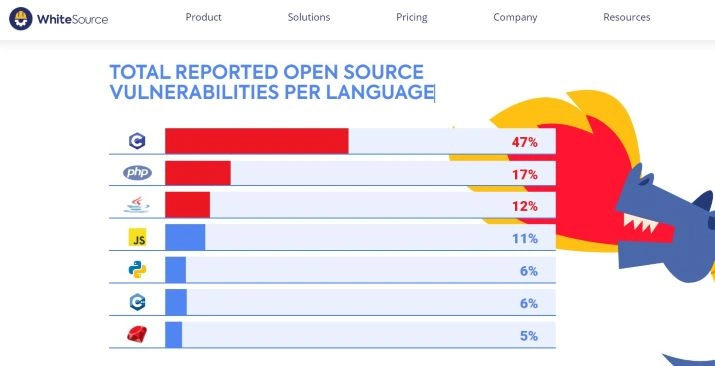
So what are the most secure programming languages? Does the most secure programming language even exist? Let's look at a report that brings a fascinating perspective to explain this problem.
The most secure programming languages — WhiteSource report
In the report "What Are The Most Secure Programming Languages?, WhiteSource selected the 7 most popular programming languages out of more than 200 and analyzed how they have changed over the past decade. They have gathered information from sources such as National Vulnerability Database, security advisories, GitHub issue trackers, and popular open-source projects issue trackers.
Although no programming language holds the title of "the most secure language," the WhiteSource report provides a comprehensive overview of popular computer languages and their security flaws.

The fundamental research questions were:
- What programming languages are the most secure?
- Which types of security vulnerabilities are most common?
- What were the findings?
Most of the popular programming languages share similar problems.
These include:
- Cross-Site-Scripting (XSS) — CWE-79
- Input Validation — CWE-20
- Information Leak/Disclosure — CWE-200
- Path Traversal — CWE-22
- Permissions, Privileges, and Access Control — CWE-264.
Although the number of detected security vulnerabilities has increased thanks to the development of diagnostic tools, at the same time, the number of high-level, critical vulnerabilities has decreased, according to the WhiteSource study.
Security of programming in JavaScript
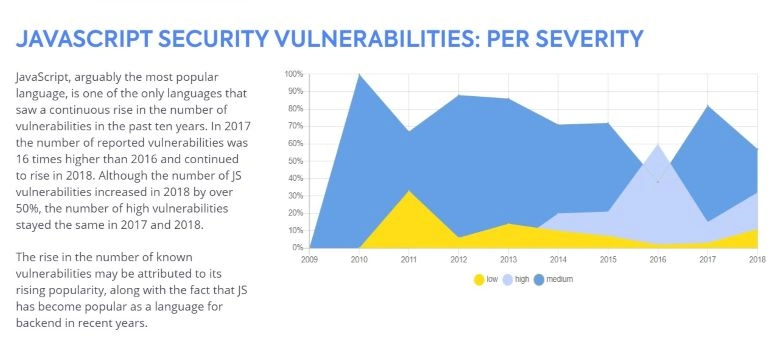
JavaScript has been one of the most popular programming languages for years. According to various estimations, it's used to write code for over 90% of websites.
JavaScript, being a very versatile language, is used by full-stack, front-end, and back-end developers.
And this directly translates into its safety rating. JavaScript also deserves special attention because it developed in terms of serverless and cloud computing.
With such big popularity and many digital products, frameworks, and libraries created in this language, it's unsurprising that the number of security vulnerabilities continuously grew over the years, endangering users.
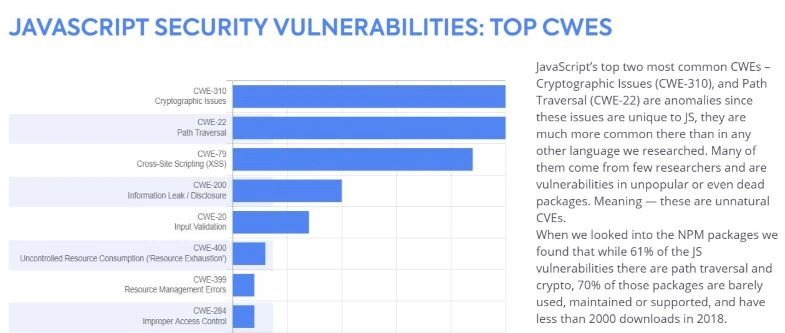
According to the WhiteSource report, security vulnerabilities that often appeared in JavaScript included the following:
- Cryptographic Issues — CWE-310
- Path Traversal — CWE-20
- Cross-Site Scripting (XSS) — CWE-79.
Security of programming in Python
Python, which gains in popularity every year, is a high-level, object-oriented language whose primary advantage is simplifying the programming process.
Moreover, Python is valued for its readability, code clarity, and easy syntax.
Python often is used to detect malicious software and perform penetration tests.
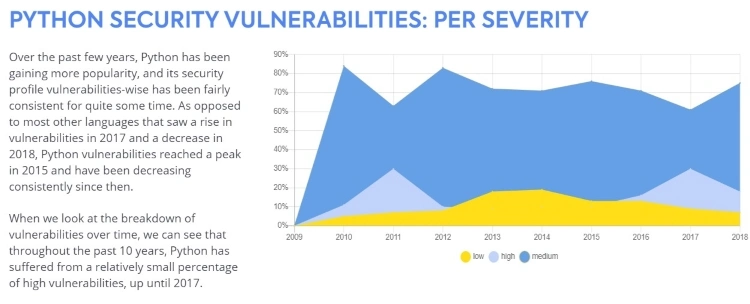
Although Python has gained in popularity — unlike JavaScript — it hasn't experienced such a significant increase in security vulnerabilities.
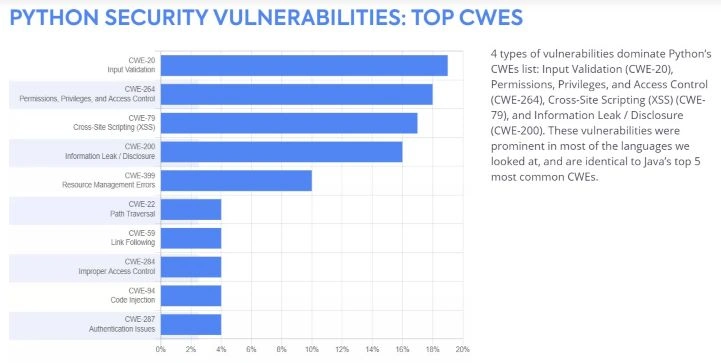
According to the WhiteSource report, security vulnerabilities that often appeared in Python included the following:
- Input Validation — CWE-20
- Permissions, Privileges, and Access Control — CWE-264
- Cross-Site Scripting (XSS) — CWE-79.
Security of programming in PHP
To put the first two programming languages into perspective, we would like to present what the WhiteSource study found about the PHP language, which, despite losing popularity, is still a widely used open-source programming language for web development.
In the report, PHP ranked second regarding the number of reported vulnerabilities out of all the languages.
According to the WhiteSource report, security vulnerabilities that often appeared in PHP included the following:
- Cross-Site Scripting (XSS) — CWE-79
- SQL Injection — CWE-89
- Permissions, Privileges, and Access Control — CWE-264.
What distinguishes PHP in the WhiteSource report from other languages is that SQL injection frequently appeared in it. WhiteSource states that many experts would consider this vulnerability a thing of the past. Moreover, the issues with maintaining high security and the number of security flaws only grow.
A fascinating conclusion from the report prepared by WhiteSource is the observation that the overview of the situation is primarily influenced by changes in the methodologies and definitions that are observed in the Common Weakness Enumeration.
Furthermore, some types of weaknesses gain strength or weaken at a given time, and it is, therefore, difficult to speak of any steady level.
This involves increased awareness of these problems and community engagement, which aims to counter them.
In conclusion, it's worth being aware of the high conventionality of category types — the best programming languages for application or user security — their relativity and dependence on the adopted criteria, time, methodology, and rank of indicators.
The best and most important programming languages for protecting applications. Summary
- Terms such as, for example, web application security often refer to all activities, solutions, technology, and processes that aim to ensure the best possible protection from malicious attacks.
- Web application security depends on regularly examining its structure and way of working.
- Application security is primarily ensured by searching and patching security vulnerabilities.
- Combined with searching for errors and shortcomings, it constitutes a set of basic actions that increase the protection of a mobile application.
- Vulnerabilities and errors in the applications or user accounts significantly increase the risk of an attack that may result in third-party access to confidential company and customer data.
- The choice of technology, solutions, tools, and means of securing applications, mobile devices, users, customers, or business owners is always determined by various and numerous factors.
- The most crucial factors influencing the security of mobile apps (e.g., data protection) include, among others: efficiency, utility, the long-term nature of the technology in question, its business profitability, budgetary matching of technology to the project, and the level of expected security of an application.
- Mobile application security is often not treated as a factor of strategic importance.
- Very often, the following matters are prioritized over application security: current technology trends, the ratio of the quality of the code to the cost of producing it, the availability of specialists in a given market, and the acceptable level of security to be achieved in a given project.
- The comparison of programming languages in terms of their security is very controversial regarding the criteria and methodology. Applications and their security are complex and variable over time problems.
- The comparison of programming languages regarding their security is always an attempt to answer the following questions: how much a given language is vulnerable to attacks, what level of security does a given language offer, and what types of attacks do you have in mind, how long resistance to attacks do you want, how frequent are the attacks, what kind of threat detection do you have in mind, and what moment in the development of a particular programming language do you have in mind?
- Most of the popular programming languages over the past decade have offered varying levels of security.
- The constantly updated and developed Common Weakness Enumeration (CWE), a list of common software vulnerabilities, is an initiative aimed at increasing the level and scope of security of mobile applications.
- Common Weakness Enumeration contains flaws and errors involving hardware or code, which, if not eliminated, can be a cause or means of launching malicious attacks exposing applications, users, and owners to a lot of damage.
- CWE is described and defined as an indicator of security tools, a basis for identifying weaknesses, and a collection of recommendations for repairs and prevention activities.
- In recent years, the number of security vulnerabilities detected has increased, and the number of vulnerabilities with a high significance level has decreased.
- In JavaScript, the most common vulnerabilities include the following: Cryptographic Issues – CWE-310, Path Traversal – CWE-20, and Cross-Site Scripting (XSS) — CWE-79.
- In Python, the most common vulnerabilities include the following: Input Validation – CWE-20, Permissions, Privileges, Access Control – CWE-264, and Cross-Site Scripting (XSS) – CWE-79.
- PHP is the only language with such a prominent occurrence of SQL Injection.
- Determining the current level of security of a mobile application and indicating a corpus of solutions protecting the applications is primarily determined by adopted methodologies and definitions.
- It's worth being aware that some types of weaknesses gain strength or weaken at a given time, and it is, therefore, difficult to speak of any steady level.
- Categories such as — the best programming languages for application security and technologies protecting applications — addressed to users of smartphones and business owners are highly conventional, vague, and devoid of strong criteria and methodological basis.





