Web Application Security is stirring up excitement and interest.
Not only in business owners but also application users, who are increasingly interested in security because they're more aware of the dangers of cyberattacks.
Security issues, along with scalability, performance, and user experience, are perhaps one of the most important matters that need special attention in designing and developing web applications.
The reason for this is quite obvious and understandable. An application that isn't adequately secured and therefore poses a risk to its owners and users is an application whose market fiasco is a matter of months.
Sooner rather than later, flawed, underdeveloped, and amateur security measures will attract trouble.
We should remember that while the scope of a company's operation may be local, its online presence is always global.
The risk of attacks always exists, it has no specific source, and it's impossible to pinpoint the area from which it may originate. That is why thinking about web application security is reasonable for any business scale.
It's also challenging to identify potential attackers. They can be individuals (hackers), organizations (e.g., organized crime groups), as well as other nations using their institutions for an attack.
Software of various kinds can also be an aggressor, which doesn't require any intentional action from a particular person. It spreads randomly like viruses.
In other words, we must always be ready to repel an attack that can come from different locations, occur on different levels, and have varying levels of complexity and damage.
The development of technology means the development of threats as well as methods, techniques, and tools to minimize, detect and eliminate them.
Nowadays, protection means not only being ready to effectively repel an attack but also a need for solid prevention.
This brings us to some key questions that we'll seek answers to in the following article. What is web application security? What are the most common threats and security vulnerabilities?
What methods are recommended for countering threats? What are the best practices for securing web applications?
These are precisely the issues we'll be addressing today.
As always, we wish you a pleasant reading!
The growing problem of Web Application Security
Before we define the concept of web application security, it's worth recognizing the nature and scale of the problem.

A good incentive for this is the Accenture report, "The state of cybersecurity resilience 2021," from which it's pretty clear that the problem of ensuring the security of applications and their users is becoming a pressing issue.
According to Accenture's report:
- The number of cyberattacks on companies is increasing every year.
- The size of budgets and investments in security are also growing rapidly.
Equally interesting, illustrative, and impressive data is provided by another Accenture report, "Cyber Threat Intelligence Report," which in turn shows that in 2020:
- More than 60% of cyberattacks involved the extortion of data.
- Ransomware intrusions caused an average of twelve days of operational downtime for applications.
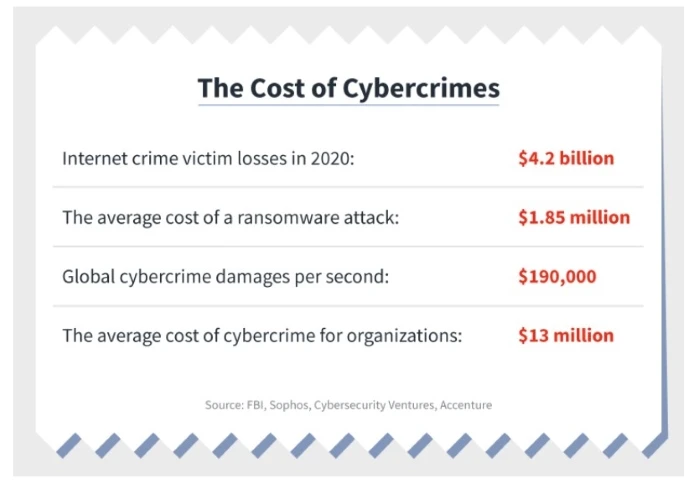
If we look at yet another Accenture report, "Eighth Annual Cost of Cybercrime Study," addressing the cost issue, we'll realize that the scale of the problem is severe.
The average repair cost after a malware attack was $2.4 million, and the average repair time was 50 days.
Current trends will intensify in the future, and all indications suggest that the cost of cybercrime will increase by about 15% each year. At least, that's according to various estimates discussed in the article "Cybercrime To Cost The World $10.5 Trillion Annually By 2025."
The overall picture that emerges from the above reports and many other sources is pretty clear.
Web application security is an issue that is already determining the market "to be or not to be," and it will become even more critical.
Simultaneously, it raises the problem of adequately allocating resources spent on security.
It also poses the problem of finding efficient, effective, and appealing solutions in terms of cost.
Malicious attacks on web applications are the source of the following:
- Material damage (such as a damaged server)
- Brand identity damage
- Financial damage
- Business damage
- Social and market damage (e.g., undermining public trust in digital products)
- Psychological damage (traumas associated with the damage caused by the attacked applications).
What is Web Application Security?
Web applications security (Web AppSec) means the implementation of appropriate mechanisms, standards, safeguards, protocols, and tools that, by working together, allow the application to operate reliably, even during a cyberattack.
When seeing the term web application security, we should think of processes, technologies, and methods of protecting servers, the infrastructure of web applications, and web services from attacks.
Web application security is mainly vital for:
- Protecting users and organizations from data theft
- Ensuring the continuity of application operation.
When we write about web application security, we also have preventive measures in mind, such as finding, fixing, and eliminating security vulnerabilities.
Primarily, we're referring to the protection of web applications with the following solutions:
- Web Application Firewalls – WAF
- Multi-Factor Authentication – MFA
- Cookies Validation
- Validating User Input
When raising the security issue, it's worth noting that it's virtually impossible to create a web application, a web service, or a mobile application without flaws.
A flawless application with no defects, imperfections, or errors is more of a concept, an ideal to pursue than a realistic possibility.
Every software has flaws, which create more or less dangerous threats. Web application security is a process in which an important role is played by the constant control of application operation, removal of errors, and elimination of potential causes of threats.
Therefore, to secure a web application, it's necessary not only to monitor it for security vulnerabilities regularly and patch them but also to continuously improve internal procedures and a collection of good practices to increase the application's security level.
What are the most popular forms of attacking a web application?
We use the term Security Vulnerabilities when a feature of an application or the ecosystem in which it operates allows someone to access or perform operations on a resource/data without the permission of its owner.

A security vulnerability is an unintentional or intentional flaw in software due to which unauthorized individuals, whether deliberate or not, can perform an operation in an application that may expose users to data loss or identity loss or prevent further use of the application.
The most common causes of security vulnerabilities in web applications are:
- Complexity (of a system) which raises the probability of errors
- Familiarity – exploiting open code, hardware whose vulnerabilities are well known
- Operating system errors
- Errors in the source code
- Incorrectly configured system components
- Poor authentication practices
- Lack of strong encryption.
An attack on a web application is often defined as an attempt to breach its security to gain access to confidential data or to use the application as a tool to launch attacks on application users or other IT systems.
Popular methods of breaking security and exploiting vulnerabilities used by hackers include:
- SQL Injections – involves the use of malicious SQL code to gain unauthorized administrative access
- Cross-Site Scripting (XSS) – also relies on injecting malicious code directly into the application to ultimately attack the user's browser and gain access to multiple functions (e.g., camera, geolocation)
- Cross-Site Request Forgery (CSRF) – involves the use of a malicious web application that performs an unwanted operation on a website where the user is logged in
- Denial of Service DoS and Distributed Denial of Service DDoS – are based on overloading the application infrastructure by generating large amounts of data and queries.
According to yet another classification, in which the main differentiating criterion is the target of the attack, we can distinguish between threats targeting:
- Customers and users of an app
- Application services
- Access layer.
Customers are exposed to threats in the form of:
- Cross-Site Request Forgery
- Cross-Site Scripting
- Session Hijacking
- Malware
- Malicious Scripts
- Certificate Forging.
The targets of attacks will very often also include components, devices, and tools without which a web application can't work.
In particular, those vulnerable to attacks are:
- Infrastructure elements
- Frameworks
- Libraries
- Plug-ins
- Internal code.
Application services are most often attacked by:
- SQL Injection or XSS
- Malware
- DoS and DDoS
- Cross-Site Request Forgery
The access layer, which allows users to authenticate and gain authorization to access an application, is a very common target of attacks.
It's estimated that over 30% of all malicious attacks on web applications are attempted through this layer.
The access layer is most often attacked by:
- Credential Theft
- Credential Stuffing
- Session Hijacking
- Phishing.
Web Application Security Testing
Performing regular, scheduled, and various tests of web applications is as much an obvious matter today as it's simply necessary.
The notion of web application security is a concept that primarily indicates the processual nature of such activities.
Web Application Security Testing is often defined as a process in which an application is tested and analyzed in terms of security, implemented safeguards, and occurring vulnerabilities.

The result of these activities is a report that determines the security level and status of the web application.
Security tests measure the safety level of web applications using manual and/or automated security testing techniques, methods, and tools.
It's worth noting that web application security isn't a permanent state; instead, we should think of it as a process.
Security needs to be continuously improved, enhanced, ensured, and verified with various tests that can detect and patch vulnerabilities.
The most common types of security tests are:
- Dynamic Application Security Testing (DAST) – these are automated tests recommended for the security testing of internal applications with low risk
- Static Application Security Testing (SAST) – is recommended for identifying errors without launching an application in a production environment
- Penetration Testing – is advised for testing applications of critical importance; its primary goal is to detect advanced attack scenarios.
Additional ways to enhance Web Application Security
Enhancing web application security isn't just about testing but also includes preventive measures designed to reduce the risk of an attack.
The minimum access policy and the rule of limited trust help to reduce risks by managing access, which should be different for various user groups. Not every user needs the same set of permissions.
The top-level permissions, as a rule, should be offered only to a narrow group of users.
Another way to counter an attack is to validate user input. The text entries and attachments in various formats are often targeted by attacks and should be validated.
Validation is often performed on:
- Data type (such as numerical data)
- Data format (e.g., conforming to XML schemas)
- Data value (such as length).
The input data is also validated in terms of its syntax, correctness, and compatibility with the business logic implemented in the application.
When it comes to validating input data, it's also worth applying the presumption of the hostility of input data until it's proven otherwise.
To prevent processing incorrect and questionable data, we need to process only correctly entered data.
Best practices and commonly recognized tools significantly enhance our application's security level. Implementing two-factor authentication mechanisms, error monitoring, soft deletion of data, GDPR compliance, and the implementation of tools that offer additional security mechanisms like AWS WAF or Shield all significantly improve the security of our application.
In addition, regular backups, encryption, and good crisis management procedures will ensure continuous and stable application development.
Web Application Security. Summary
- Web Applications Security is an issue attracting the interest of many groups – not only business owners but also users of web and mobile applications.
- Security and safety of web and mobile applications (along with scalability, performance, and user experience) are among the most important issues.
- A web or mobile application that isn't adequately secured is an application that doesn't have a bright future on the market.
- Application users are increasingly paying attention to the level of security implemented in applications.
- The company's scope of operation is irrelevant when it comes to ensuring the security of web and mobile applications.
- Being present on the Internet, having a website (www), web, or mobile application means being global. And this means that the risk of attacks is always there and doesn't have a specific source.
- The security of web or mobile applications is advisable regardless of the size of an organization.
- Every organization should be prepared for a possible attack, which can come from different locations, occur at different levels, and have varying levels of complexity and damage.
- According to numerous cyclical reports, the number of cyberattacks on companies is increasing every year. The number of attacks entails an increase in the size of budgets and investments in security.
- According to various estimates, cybercrime costs will increase yearly.
- Web application security (Web AppSec) means the implementation of appropriate mechanisms, standards, safeguards, protocols, and tools that, by working together, allow the application to operate reliably, even during a cyberattack.
- Web application security includes processes, technologies, and methods of protecting servers, the infrastructure of web applications, and web services from attacks.
- Web application security also encompasses preventive measures such as finding, fixing, and eliminating security vulnerabilities.
- Web application security is a process in which an important role is played by the constant control of application operation, removal of errors, and elimination of potential causes of threats.
- We use the term Security Vulnerabilities when some feature of such an application or the ecosystem in which it operates allows someone to access or perform operations on a resource/data without the permission of its owner.
- An attack on a web application is often defined as an attempt to breach its security to gain access to confidential data or to use the application as a tool to launch attacks on application users or other IT systems.
- Malicious activities usually target application users, application services, and access layers.
- The targets of attacks will very often also include components, devices, and tools without which a web application can't work.
- Web Application Security Testing is often defined as a process in which an application is tested and analyzed in terms of security, implemented safeguards, and occurring vulnerabilities.
- Security needs to be continuously improved, enhanced, ensured, and verified with various tests that can detect and patch vulnerabilities.
- Enhancing web application also includes preventive measures designed to reduce the risk of an attack.
- The minimum access policy and the rule of limited trust help to reduce risks by managing access, which should be different for various user groups.
- It's recommended to implement the presumption of the hostility of input data in the validation process.
- Best practices and commonly recognized tools significantly enhance our application's security level.







