What to do if you don't want to spend $300 on a certificate? What to do if you need more than one certificate? We decided to use free SSL certificates and streamline the management of multiple certificates with our custom tool. We save several thousand dollars a year and provide users with high security.
An SSL certificate is like a guardian protecting access to the data transmitted between a website and a web browser. Data from our servers is transported to a user, but with the help of an SSL certificate, this transfer is encrypted. Thanks to this, we protect our users against some types of attacks (man-in-the-middle, session hijacking, etc.).
2018 brought changes to the entire Web. Chrome, followed by Firefox and Opera, started to signal if a visited website is protected.
This message means that the owner of a site didn't install an SSL certificate. If that weren't enough, websites without an SSL certificate installed are treated by Google as worse in search results. In other words, their visibility decreases, and Chrome discourages users from entering them.
Some companies have been forced to buy SSL certificates because of this. And it forced us to think about how to meet the requirements of a technological giant without spending a fortune every year.
An SSL certificate is a small file on a server
In practice, an SSL certificate is a small file we put on our server. It consists of a private and public key through which we ensure the security of communication with a website. We need to remember that it's not meant to protect our site but to secure the connection between a website and a visiting user.
How much does an SSL certificate cost? Besides free certificates, we also have those whose price ranges between $8 and $1000 a year.
SSL certificate's validity is a pain point for companies and IT administrators
In the beginning, we encountered a serious problem. In "Let's Encrypt," which we use to generate free SSLs, a certificate is issued for a maximum of three months.
This means that we need to renew the certificate after three months, which is a bit problematic for us. We take care of many websites of different clients, so keeping an eye on the expiration dates of certificates was necessary. Of course, we can try to automate the renewal of certificates, but it's not always possible. The diversity of clients' infrastructure, restrictions on security access requirements, different operating systems, and other complications in some cases required manual updates of certificates.
Failure to renew a certificate not only leads to security problems but also damage to the brand's image, and in the case of platforms that actively sell products, it carries a measurable financial loss because every browser effectively blocks access to a site whose certificate expired (opening the site is still possible but problematic).
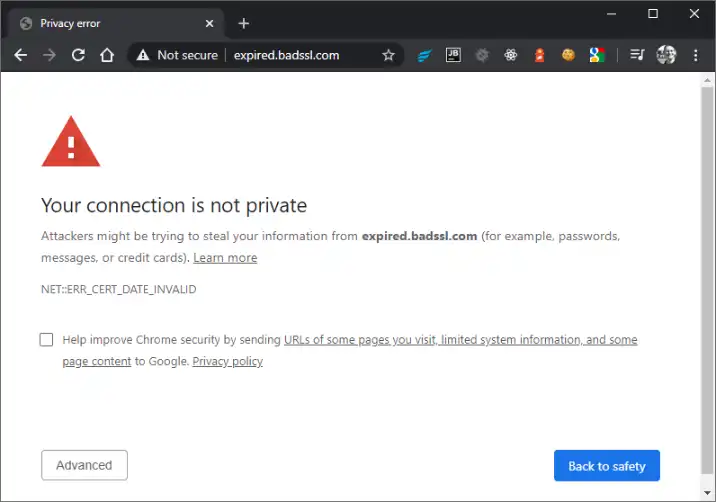
Cyclic tasks reminding us about expiring certificates on particular domains? Keeping track of certificate expiration reminders sent by Let's Encrypt? Possible, however, potentially leading to errors, and it's a bit unprofessional, especially in the case of hundreds of domains supervised by different teams or, often, client's administrators outside of our company.
We started looking around for services that solve this problem and are available in a subscription model.
We counted very quickly that with many domains, the cost would be hefty. Besides, the logic of these tools didn't always correspond to the organizational structure of our company or the needs of the client. And it would be another subscription-based SaaS to the collection of services used by the IT department. We chose a different way.
Custom tool for controlling SSL certificates
We wrote a custom tool that reminded us of expiring certificates on domains and sites managed by The Story.
Instead of relying on setting reminders in a calendar or on a list of tasks, we created a simple application that regularly asks our websites and checks the expiration date of SSL certificates.
If the software detects an expiring certificate, then an email is sent to interested parties (DevOps, client, or project manager) with a list of servers and domains on which it's necessary to update SSL certificates. Messages will be sent until the certificate is renewed or SSL monitoring is turned off for the particular website.
A simple method in Python that returns the number of days left until a domain certificate expires:
import datetime import socket import ssl from ssl import CertificateError def expire_in_days(self, domain_name): ssl_date_fmt = r'%b %d %H:%M:%S %Y %Z' now = datetime.datetime.now() context = ssl.create_default_context() expiration_days = 0 conn = context.wrap_socket(socket.socket(socket.AF_INET), server_hostname=str(domain_name)) conn.settimeout(3) try: conn.connect((self.domain, 443)) ssl_info = conn.getpeercert() expiration_date = datetime.datetime.strptime(ssl_info['notAfter'], ssl_date_fmt) expiration_days = (expiration_date - now).days except IOError: pass except CertificateError: pass return expiration_days
How an SSL certificate works on an example of Let's Encrypt
How does Let's Encrypt work? We launch the appropriate tool on the server and receive a Secure Socket Layer certificate. We go through verification, which ensures that we're the owners of a given domain (there are multiple methods of verification to choose and we can select an appropriate one for every project). As a result, we receive a certificate that protects the communication between a user and a website.
There are also certificates of a higher level which are more expensive. Such certificates require additional verification of the company to which a website belongs. However, in exchange, we get an insurance policy. The insurance provider is the issuer of the certificate, which pays compensation to the user if our website has exposed the user to losses.

Custom corporate website. Check it out!
SSL certificates — why do they pay off?
As a developer, I recommend installing SSL certificates on every website. It's not a complicated process, and there are free certificates on the market.
In the case of transaction systems, I recommend using payable certificates (SSL EV/OV) because of the green padlock, which increases the credibility of the website among users and the security of payments (remember about compensation!).
For domain and subdomain management, purchasing a Wildcard SSL certificate will be more beneficial. For one fee, you can secure your main domain (e.g., certificates.com) and all its subdomains — that is, URLs that have other characters before the main domain, e.g., a.certificates.com, b.certificates.com.
Hero shot: Richard Patterson / Flickr.com / Bit.ly/2wiwQ9c / CC BY 2.0
Thanks for reading! We encourage you to share the article!
Disclaimer
The sample prices presented in the article do not constitute a commercial offer within the meaning of the Polish Civil Code.







